Managing vulnerabilities is a critical aspect of regular server and service maintenance. Timely installation of vendor patches, bug fixes, and secure configurations are essential steps to prevent threat actors from compromising your server.
The IT Security team ensures your server’s security by notifying you of any issues that require attention. We use the Vulnerability Management Standard Operating Procedure to alert you to missed patches or necessary TLS configuration updates.
Scope
The Vulnerability Management Standard Operating Procedure is generally applicable to any system on the McMaster University network, or any system managed by or on behalf of the University. In short, any server that handles McMaster information.
More specifically, this procedure is intended to mitigate vulnerabilities on high-risk systems, such as:
- Systems to which anyone on the internet can connect
- Systems that collect credentials or leverage McMaster centralized authentication and authorization
- Systems that handle credit card transactions
- Systems that handle personally identifiable information (PII), personal health information (PHI), or any information that can be classified as confidential or restricted.
Workflow
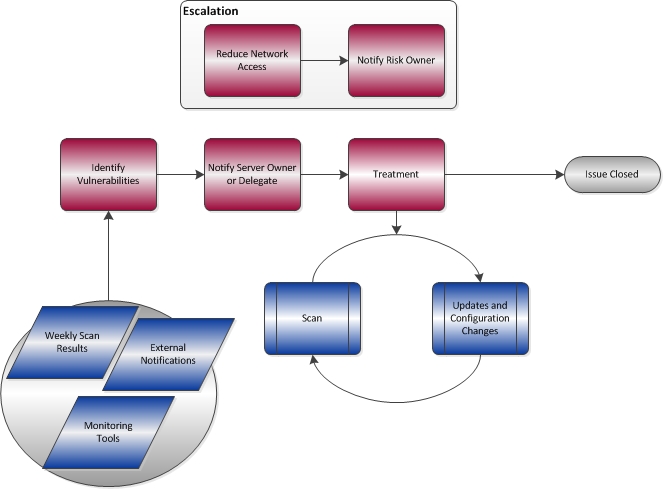
Identify Vulnerabilities
The IT Security team uses a number of tools and resources to help identify vulnerabilities on high risk systems on the McMaster network. Some of these tools include weekly vulnerability scans, or CCIRC notifications.
Notify Server Owner or Delegate
When a vulnerability has been identified on a high risk system, the IT Security team will send a notification to the system owner, and also to the technical resource to whom system maintenance responsibilities have been delegated. We will include important details about the vulnerability, such as the impact of an exploit. We will also provide our recommendations, or the recommendations of trusted experts, to mitigate the risk of exploit.
Treatment
After the owner or delegate has treated the risk, by either changing the configuration or installing an update, the IT Security team will perform follow up testing to ensure that the treatment was successful.
Other treatment options include reducing the exposure by preventing public access to the server, or decommissioning the server if it is no longer in use.
Escalation
In the event that the server owner or delegate fails to respond to the notification, or to treat the risk, in a timely manner, the matter may be escalated to the risk owner. The risk owner is the executive responsible for the department to which the server owner belongs.

