By now you have received a notice or news from UTS (IT-Security and Enterprise Networks Teams) indicating that a Next Generation Firewall (NGFW) is being deployed on our network to monitor network traffic. This Q&A aims to clarify and shed further light on the exact method/mechanism used to deploy this new technology.
-
-
Where is this device going to be located at the network level?
-
The campus network receives Internet connectivity via multiple providers. The NGFW will be connected at the Internet edge of our network, where the main pipe to/from the Internet is located. As such it will have the opportunity to let pass and examine all the traffic that comes in or goes out of our network towards the Internet.
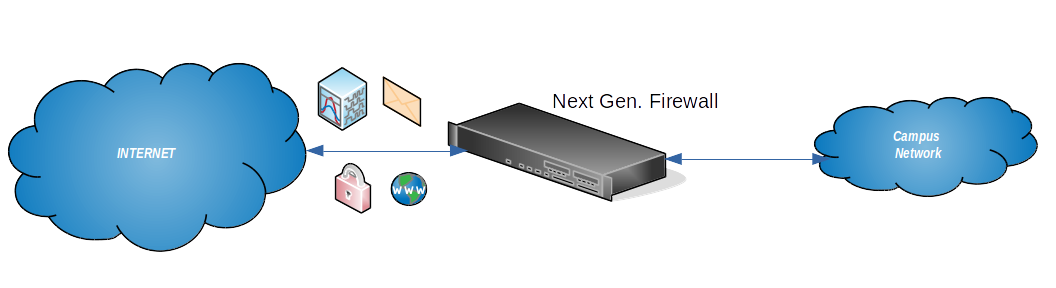
As a result of this particular setting, only traffic that comes in/goes out of the internal network will be affected by the technology. Understanding this is important because this means that traffic that traverses the internal network will not be affected.
This can be better understood with some examples:
| Example | Impact |
|---|---|
| My Server is visible to external networks (webserver or similar) | Traffic coming to the server will pass through the NGFW |
| I have a network printer that my office staff uses | Traffic to the printer is internal and therefore does not pass through the NGFW |
| My staff exchanges files across the (internal) network | Traffic is internal and therefore does not pass through the NGFW |
| I store and share files on McMaster’s MacDrive solution | Traffic is internal and therefore it does not pass through the NGFW |
| I store files via a cloud based service (Google drive or similar) | Traffic goes to external network/s and will pass through the NGFW |
| I visit many websites on the Internet | Traffic to websites external to McMaster go out of our network and will pass through the NGFW |
| I send and receive a lot of emails | Only emails messages involving external parties would pass through the NGFW |
| I am connected to the network via wireless | Wireless is still internal therefore it does not pass through the NGFW |
| I use wireless to connect to external resources, such as the Internet | Traffic goes to external network/s and will pass through the NGFW |
-
-
What is the purpose of this device compared to technology currently already in place such as firewalls, routers etc.?
-
Next Generation Firewalls are sophisticated devices designed to detect anomalous behaviour right “as it happens” as opposed to “after the fact”. Previous security efforts up to this point have been, for the most part, reactive in that we discover bad activity much later when contamination or intrusion has already taken a foot hold on our internal network. With a NGFW, we could be proactive, more efficient and faster when mitigating or responding to security incidents.
-
-
What will the NGFW do when it encounters “bad traffic”?
-
The NGFW is not meant to block or impede normal operations or activity that occurs routinely. Instead, it is supposed to catch anomalous activity that might be known or not to users. 4 specific set of rules will be implemented incrementally throughout the month of July to establish a baseline security. The details of these rules will be timely disclosed to technical campus partners.
-
-
When and how will I know that the NGFW has been installed and is monitoring my traffic?
-
The deployment of the NGFW will occur in two phases:
Phase 1
On July the 3rd the NGFW will be installed on the network at the above shown location. On this date the NGFW will be set to intercept traffic at the perimeter of our network and let traffic pass unrestricted – no inspection of traffic will be performed at this particular point in time.
Phase 2
This phase will unfold in 3 stages throughout the month of July and specific dates have been selected to incrementally apply rules to address the following:
-
-
- Threat Prevention (Intrusion Protection) – July 12th
- Malware Prevention – July 23rd
- URL Filtering – July 26th
-
Details on how each of these rules are deployed will appear as linked content in the 3 stages above.
-
-
How will the NGFW treat encrypted traffic?
-
Encrypted traffic will be monitored by the NGFW but since the device is not going to act as a Man-in-the-Middle, it will not inspect within the encrypted traffic. This is done so in order to protect the privacy of communications that rely on the use of any form of encryption, be it SSL, SSH or similar. This does not mean that the encryption being used does not suffer from issues. If the specific resource using encryption is not properly configured, it could be vulnerable to attacks. For more information on Encryption Security see this link.
-
-
Will the NGFW be tracking my web browsing activity?
-
From the privacy perspective, the NGFW will not keep track of website browsing activity but from the security perspective, it will still examine the traffic and make determinations if the traffic is deemed malicious or harmful. A specific feature called ‘URL Filtering’ will be turned on to accomplish this. If the web traffic is encrypted, it will not be intruded upon but the domain being visited may be correlated against malicious lists that the NGFW will use for this purpose.
-
-
Want kind of tests are expected of me to perform considering how the NGFW is configured?
-
All technical groups across campus are being asked to identify and report applications or resources that might be affected by the deployment of this device. The resource or application will be impacted if there is some sort of communication involved with external networks and as such, the test/s should be on those features that use this connectivity. For example, if you are responsible for a server hosting websites exposed to external networks, ensure that the current functionality is still present. If you connect via Remote Desktop to an external server or from outside to an internal server ensure that this is still working.
-
-
How will the NGFW affect the campus VPN connections?
-
Traffic that uses the campus VPN will be affected by the NGFW but since this traffic is encrypted, it will be recognized but not interfered with in any way or blocked.
-
-
What can do if I notice or suspect that the NGFW has blocked my traffic?
-
The first step is to confirm that the issue is caused by the NGFW. Please refer to question # 1 to determine if your traffic is passing through the NGFW. If this is indeed the case, the issue might depend on the type of activity involved. Are you trying to establish communication with an external location? What is the event that is leading you to think that the NGFW might be blocking your activity? Once a clear picture is obtained, you can contact the UTS Help Desk and report the incident and log a ticket.
-
-
What can I do if my application or resource is sensitive to latency?
Certain applications or services such as Video Conferencing or VoIP, are susceptible to latency and jitter. As such, voice and video packets cannot be dropped, delayed, or delivered inconsistently. If required, the NGFW can be set to prioritize voice and video applications to guarantee a certain minimum bandwidth and level of traffic for a particular IP address or group of IP addresses.
-
As a technical Liaison, can I (or my team) receive alerts or notices with regard to traffic that has been flagged as suspicious in my area?
-
This will not be enabled during the initial stage/deployment but once the NGFW is solidly established and performing as expected, we will be looking for mechanisms to send alerts directly to affected groups.
-
-
Can information be obtained regarding the user or login id involved in the suspicious activity?
-
Information about logons involved in certain activities is useful to conduct investigations as to what system or user could be attached to a particular incident. User-id is a standard feature of the NGFW that will allow technical folks to narrow down to what IP was involved in a particular activity such as network connections or Kerberos ticket granting sessions.
