Malware Prevention Policy
This is the second policy to be enabled and it is going to have the most impact on end-point systems (client machines) as it is designed to prevent viruses, malware, command & control (C2) activity, malicious code execution and spyware, particularly when these systems are making connections to external networks. This policy is made up of 3 inspection profiles:
- Antivirus Profile
- Anti-Spyware Profile
- Wildfire Analysis
This inspection profile will block known malicious files (malware, ransomware bots, and viruses) as they are coming into the network. The profile will accomplish this by making use of decoders that will prevent malware from being transferred over six protocols: HTTP, SMTP, IMAP, POP3, FTP, and SMB. Aside from these, Wildfire analysis will also be enabled on these six protocols to enforce an action based on wildfire signatures. Common ways for users to receive malicious files include malicious attachments in email, links to download malicious files, or silent compromise facilitated by Exploit Kits that exploit a vulnerability and then automatically download malicious payloads to the client device.
The Anti-Spyware profile is designed to detect and prevent command and control traffic activity initiated from malicious code running on a server or endpoint and also prevent compromised systems from establishing an outbound connection from the network. If a malicious connection is detected, this profile will perform DNS sinkholing to prevent systems from accessing known malicious domains and capture packets to help track down the endpoint that attempted to resolve the malicious domain if necessary. This profile will make use of the NIST based CVE/CVSS severity classification to enable the detection of medium, high, or critical severity threats.
Wildfire is a feature of the NextGenFW that allows for the automatic submission of unknown threats to the cloud for analysis. This is necessary because new or unknown threats are increasingly sophisticated and targeted and they often go undetected until long after a successful attack has occurred. Also, it is important to recognize that the threat landscape is ever changing and the risk of unknown threats lurking in the files we use daily such as PDFs, Microsoft Office documents (.doc and .xls files) is constantly growing.
Considerations for Systems Administrators
This rule will have a significant effect on client based computer activity. Keep in mind that only traffic to/from external networks will pass through the NextGenFW and if malicious, get blocked. In a typical scenario, client systems are not normally exposed to external networks but they have the ability to connect to external hosts without restriction via web browsing, file transfer, remote desktop access, email etc. When they do that, they might come across malicious websites, files or schemes that have been purposely designed to trigger an action that might lead to a compromise. If this type of activity is detected, it will be flagged and/or blocked depending on the severity of it. As a result, the affected used might receive an alert web page similar to the one below:
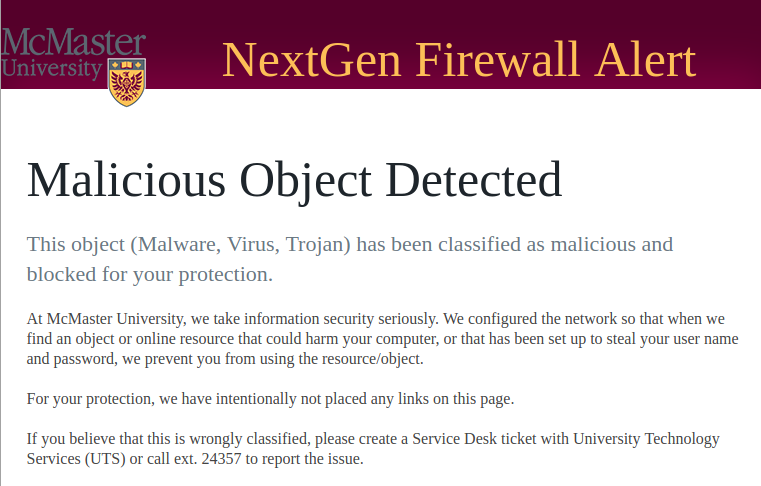
If this web page is received and you think that the activity is considered legitimate, follow the instructions on the page to report the issue. If the system attempting to access the malicious object has a local antivirus solution such as TrendMicro or similar, that solution might intercept the attempt and give a localized response page that is unique to the antivirus or anti-spyware solution being used. If the object passes that control, it will then go through the NextGenFW and it will get picked up at that point. Similarly if a malicious object is received via email, the University’s email system might pick up the threat by its own antivirus solution and if not, the NextGenFW will block it.
