URL Filtering Policy
This is 3rd and final policy being enabled and it will have an impact on client and server activity. This feature prevents access to web content that has been classified as high risk or being malicious. The NextGenFW uses a classification based on categories which in turn, rely on public and/or paid-for blacklisting services. Blacklisting depends on observations of websites as being malicious or performing a dangerous activity such as hosting malware or content that can be used to exploit systems. If a workstation is trying to access a website, URL Filtering comes into action by examining the URL against its own security controls. The same procedure is used if a server is trying to access a website on the internet.
For this feature to work, blocking categories need to be selected. These are the categories we have decided on enabling, given that they are quite obvious and affect everyone accross the board:
- Malware – Sites known to host malware or Exploit Kits
- Phishing – Sites known to host credential phishing pages or phishing for personal identification
- Command and Control (C2) – URLs or domains used by malware to communicate with an malicious remote server to receive attack commands or exfiltrate data.
Other categories exist such as copyright-infringement, extremism, alcohol-tobacco-drugs related, etc but they are being set to allow traffic [not block access] at this point. This could change in the future depending on policies or regulations and will be timely communicated to the campus community.
Considerations for Systems Administrators
Keep in mind that only traffic to external networks will pass through the box and if malicious, get blocked. In a tipical scenario, client systems are not normally exposed to external networks but they have the ability to connect to external hosts unrestrictively via web browsing. The same applies to servers as they also might need to navigate to external web resources for a variety of purposes. Be aware that, further to blocking, there is a custom web page that will be displayed when a web resource is being blocked. This web page will appear to the web page visitor instead of the intended target site. This block page is meant to alert the user that they are visiting a site that may pose a threat. The block alert web page is similar to the one below:
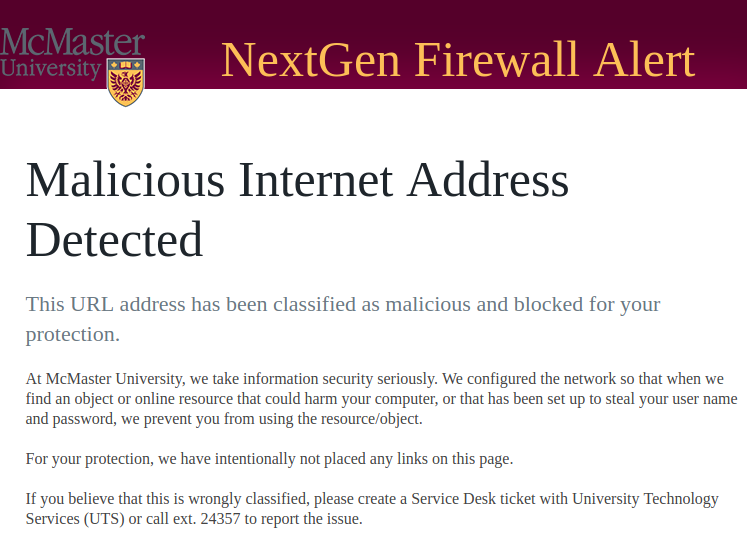
If this web page is received and you think that the activity is considered legitimate, follow the instructions on the page to report the issue.
