The External Server Access procedure is in place to ensure that any IT resource (server, network appliance or IT device) is in a safe state before it gets exposed to networks external to McMaster University’s campus network. To obtain external access, device owners must submit a request using the UTS service desk tool and log in a service ticket. Requests must include the public IP address and the service ports to be exposed to the internet for public access. The request must also include a brief description of the purpose and function of the server. The IT Security Team then reviews the request and performs a security evaluation of the server or service. The evaluation consists of security tests designed to assess the security posture of the device and make recommendations and adjustments if necessary. If issues are identified during the vulnerability assessment, these are summarized and forwarded to the service owner, along with remediation recommendations. Follow up assessments are performed as the server or service is updated and becomes sufficiently remediated. The procedure is is also designed to ensure that IT administrators are performing their due diligence in protecting resources based on a base line security. Several questions around hosting practices, device hardening, and privacy are also posed to device owners. After the resource has passed all the tests, the DNS name of the device is propagated outside of the campus network and exceptions are included on the main campus firewall to allow for external network visibility.
Security Evaluation Workflow
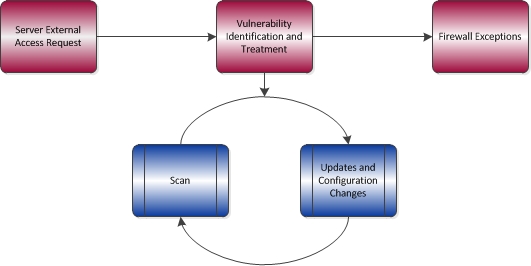
It is important to note that all publicly facing servers and services (i.e., those for which exceptions have been made on the perimeter access control list) are subject to ongoing periodic vulnerability assessments. If issues are discovered, they will be notified to resource owners for remediation.
