Sometimes it is necessary to access someone else’s private data at work such as email, voicemail or Office365. Perhaps they are on vacation, extended leave, or have left the organization, and there is critical information about a business process in their inbox that needs to be recovered. Requests such as these must be approved by either the Provost/Vice President (Academic), or by the Vice President (Administration). They may also be reviewed by the Privacy Officer to ensure that all efforts are made to protect the privacy of the account holder. The Information Security Policy addresses this type of request in statement 36, so the procedure applies to any organizational electronic account covered by the policy. This includes any IT managed service where a person can save or create private information. Some examples include:
- Voicemail
- “Home” drives, MacDrive, or MacDrop accounts
- Office 365 environments such a Team channels, Chats etc
ACCOUNT ACCESS AUTHORIZATION WORKFLOW
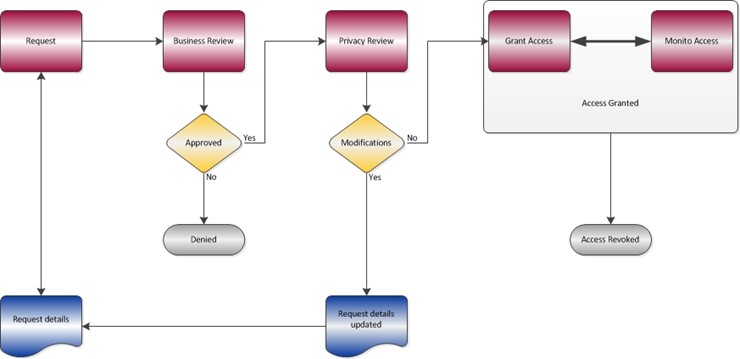
It is the responsibility of the requester to gain approval for access to another person’s account and requests must include details about the information that is required, why it is required, and for how long access to the account is needed. Requests should be forwarded directly to the appropriate Vice President for review and approval. Once approved the request is forwarded to the University Privacy Officer, who then has the discretion to recommend additional constraints. For example, the Privacy Officer may reduce the amount of time that the account can be accessed, or require that all access is monitored by another party. The service provider (i.e., UTS or any other unit providing similar access) is responsible for providing the access, and ensuring that all recommended constraints and controls are applied. For example, University Technology Services would be responsible for enabling access to an Email account, applying the constraints and controls, and revoking access when the request expires. The IT Security team will review and monitor all requests to ensure that every effort is made to comply with the recommendations of the authorizing Vice President and the Privacy Officer.
